Submitting a Microsoft Edge extension to the Microsoft Store
This is a bit of a rant, and a bit of a process documentation. I'm trying to submit the Service Worker Detector browser extension to the Microsoft Store, so it can be one of the Edge extensions everyone can easily install via a few mouse clicks. I have to say, the process is somewhat involved.
To start, it's whitelist only, so you have to apply via the extension submission form, which I did. For me, nothing really happened for a long time, so I chased down someone from the helpful @MSEdgeDev team who pulled some internal strings. Ultimately I got an email invite that I may now submit to the Store. While you can develop and test extensions locally mostly the Chrome way (that I am quite familiar with) by just loading the extension in developer mode, the process gets more complex for the actual Store submission (and required testing):
- First, you need to package the extension with ManifoldJS so it becomes an app, so far so good.
manifoldjs -l debug -p edgeextension -f edgeextension -m service-worker-detector/manifest.json manifoldjs -l debug -p edgeextension package SWDetector/edgeextension/manifest/ - Next, you need to test the resulting app package locally with the Windows App Certification Kit, also no problem. I just went for the interactive way with the graphical user interface tool. This test caught an issue with icons, where the syntax
"browser_action": {"default_icon": "icon.png"}or"page_action": {"default_icon": "icon.png"}would not work, but where explicit sizes are required instead. - Then, you need to create and export a self-signed certificate (the CertStoreLocation parameter actually ends in just "My", it's not a typo):
This returns a thumb ID that you need for the export step:New-SelfSignedCertificate -Type Custom -Subject "CN=SUP3R-S3CRET-ID-TH1NG" -KeyUsage DigitalSignature -FriendlyName "Thomas Steiner" -CertStoreLocation "Cert:\LocalMachine\My"$pwd = ConvertTo-SecureString -String mySecretPassword -Force -AsPlainText Export-PfxCertificate -cert "Cert:\LocalMachine\My\SUP3RS3CR3TTHUMBPR1NT" -FilePath self-signed-certificate.pfx -Password $pwd - You need this certificate in order to sign your app package created by ManifoldJS, which requires you to download and install the Windows 10 SDK (and obviously an actual Windows 10 installation). Windows PowerShell would not recognize the installed SignTool, so I had to use the explicit path:
& 'C:\Program Files (x86)\Windows Kits\10\bin\x64\signtool.exe' sign /fd SHA256 /a /f self-signed-certificate.pfx /p password edgeExtension.appx - Ultimately, you need to add the self-signed certificate to your trusted root certificates, but it didn't work as described, so I ended up right-clicking the certificate file in Windows Explorer and fat-fingering around in the trust settings in the Details tab until it worked and I could install the Edge extension
.appxfile by double-clicking it.
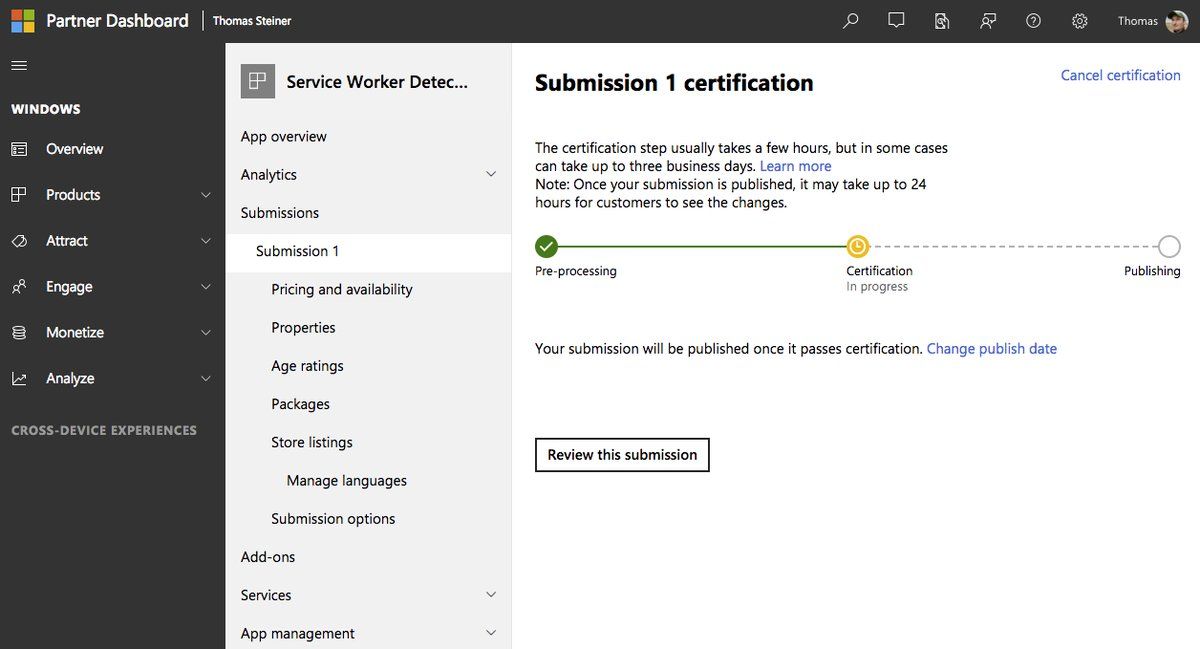
I'm now in the third iteration with their store review team where it's all working fine for me locally, but where they say it crashes on their side. Let's see how it ends. I guess the core issue is that ManifoldJS can do a lot of things to shield me from something, something Windows UWP apps, but where eventually you still need to read the UWP packaging docs for the Microsoft Store submission that are clearly not written with extension developers in mind, but rather for regular Windows app developers.
Oh, and another thing I just realized: Edge doesn't know the <details> and <summary> elements. It used to work and "[t]he implementation of this feature had shipped, but its quality was found lacking, hence this implementation was removed before Edge shipped last release. There currently [as of January 22, 2018] isn't [a] plan [Francois R. from the Microsoft Edge Team is] aware of to bring the feature back in the next update." Sad. It is, however, mentioned as Under Consideration on the corresponding Edge Platform status page with high priority, so here is hoping…
